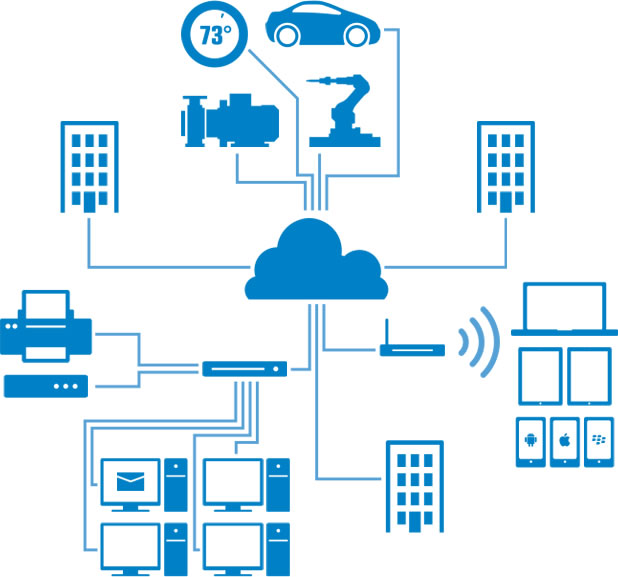
The Internet of Things is here. Highlighted by smart robots, smart televisions, smart health monitors, smart door locks, etc.. Whether by cable or Bluetooth or WiFi, nearly everything is interconnected, perhaps to smart phone, perhaps to a cloud service. From a consumer or business customer perspective, the Internet of Things is convenient and appealing. It’s also not inherently safe, not as it exists today. And that is scary.
The fundamental problem is about the uncertainty and risks of scaling complexity. We may find ourselves facing unexpected consequences by adding billions of relatively simple devices to our already complex Internet.
The first big difference lies in the sheer number of devices that could be, and eventually will be, connected. The world’s population is around seven billion people, and already there are many more devices than that connected to the Internet – although estimates seem to vary considerably. According to IDC’s estimation the number of connectible devices approaches 200 billion while the number of sensors (e.g., the accelerometer in a smart phone) that track, monitor, or feed data to those things is already more than 50 billion, with scientists talking about trillion-sensor networks within 10 years. Of those 200 billion things around 20 billion are already connected, and the number is predicted to reach 30 billion connected devices by 2020. So the first problem is not so much about the impact of any particular thing as about the possibility of unpredicted responses or vulnerabilities emerging out of sheer complexity.
The second big difference, and the one posing more immediate risk, is the fact that most of the devices now being connected are new to the IT arena. Whereas each new computer added to the Internet comes with some degree of malware protection built into its operating system, things like smoke detectors, security alarms and utility meters come from a different culture: traditionally they were either autonomous units or else, if they were connected, it was on a closed, dedicated network. Fire alarms were installed by one company, control and instrumentation networks came from a different vendor, the electricity meter was installed by the power supplier and none of these networks overlapped. While computers and IT systems have for many years been fighting off attacks, none of these simple devices joining the IoT have inherent defenses and they remain wide open to cyber-attack.
The risk is not only that the particular function could be compromised – say fire alarms disabled before an arson attack – but the IoT could provide a weak link or point of entry to an otherwise strong security chain. The infected fridge continued sending out spam mail without drawing attention to itself, because its normal operation was not affected. Despite this relative vulnerability, the most publicized attacks so far on IoT control systems have penetrated the system via IT: attackers using simple phishing-style means to breach the perimeter and then target privileged access accounts. As well as gaining access to databases and high value systems, this approach lets them use the same privileges to reach control systems and whole new opportunities for sabotage and cyber war.
That brings us to the third difference. A lesser difference, but potentially the most dangerous of all, is that many of the things joining the IoT have more of a direct physical role than the computers, game consoles and databanks currently populating the Internet.
So the IoT adds enormous extra scale to the already crowded Internet, and it also adds extreme diversity. On the one hand we are networking highly critical systems: industrial and utility grid control systems that could cause widespread damage or economic harm if breached; critical healthcare and remote medical devices containing sensitive personal data or responsible for life support; navigation and control systems for connected cars, air traffic control and so on. At the other extreme we have small low-cost monitoring devices, meters, wearable devices, simple switches for remote control of household lighting etc.
With such a range of devices it would be unrealistic to insist that every “thing” joining the IoT should have its own built-in defenses. The latest malware signature has some sixty million records and to be sure of identifying it by current pattern matching techniques would require 3-4 Gb RAM. A more sophisticated defense is provided by behavioral analysis – studying how the code behaves when quarantined in a “sandbox” environment. Such analysis of behavior for signs of malignancy is what computer scientists call an “NP Complete” problem – or what the layperson would call “extremely difficult.”
Reducing operational costs is one major driver for IoT connection – so adding sophisticated cyber-security to a ten-dollar switch would be hopelessly uneconomical. There is no way that we can realistically defend the IoT on the militia model, where every device is armed against attack – so how is it possible to provide adequate protection across such a vast and diverse cloud?
The most promising approach so far to securing the cloud, and so the IoT, is to adopt Wedge Cloud Network Defense™, which considers the traffic flow as a virtual network, rather than a string of hardware elements, and so defines a distinct “security layer” to orchestrate Security as a Service.
Today’s Internet has been compared to a water supply without any guarantee of purity, leaving responsibility for filtering and sterilizing the water to the customers. Internet users are expected to install their own anti-virus software, firewalls and other forms of security. Cloud Network Defense™ allows network operators to provide traffic that is already decontaminated – so even the most humble connected switch on the IoT could benefit from the most sophisticated security that would be provided by the network itself.
When it comes to the Internet of Things, consumers and business customers can’t manage security on their own. The IoT can’t be secured at the end node. If the Internet of Things is going to be safe — as well as compelling — securing the networks and the back end is not a luxury. It is a necessity.